Table of Contents
ToggleHey Cyber Crusaders! Ready to step into the exciting world of information security? Look no further than the Certified Information Systems Auditor (CISA) certification! It’s not just a fancy acronym – it’s your ticket to becoming the Sherlock Holmes of the digital age. Let’s dive into why having CISA up your sleeve is like having a magnifying glass for your IT career.

What is a Certified Information Systems Auditor (CISA)?
The Certified Information Systems Auditor (CISA) is a globally recognized professional certification in the field of information systems auditing, control, and security. It is awarded by ISACA (Information Systems Audit and Control Association), a nonprofit professional association for IT governance, risk management, and cybersecurity professionals.
Image source: www.shiksha.com
CISA certification is designed for individuals who audit, control, monitor, and assess information technology and business systems. The certification validates the skills and knowledge necessary to ensure the confidentiality, integrity, and availability of information systems within an organization.
Key Components of Certified Information Systems Auditor (CISA)
The Certified Information Systems Auditor (CISA) certification covers a range of knowledge domains, reflecting the diverse skills and expertise needed by professionals involved in information systems auditing and security. The key focus areas of CISA certification include:
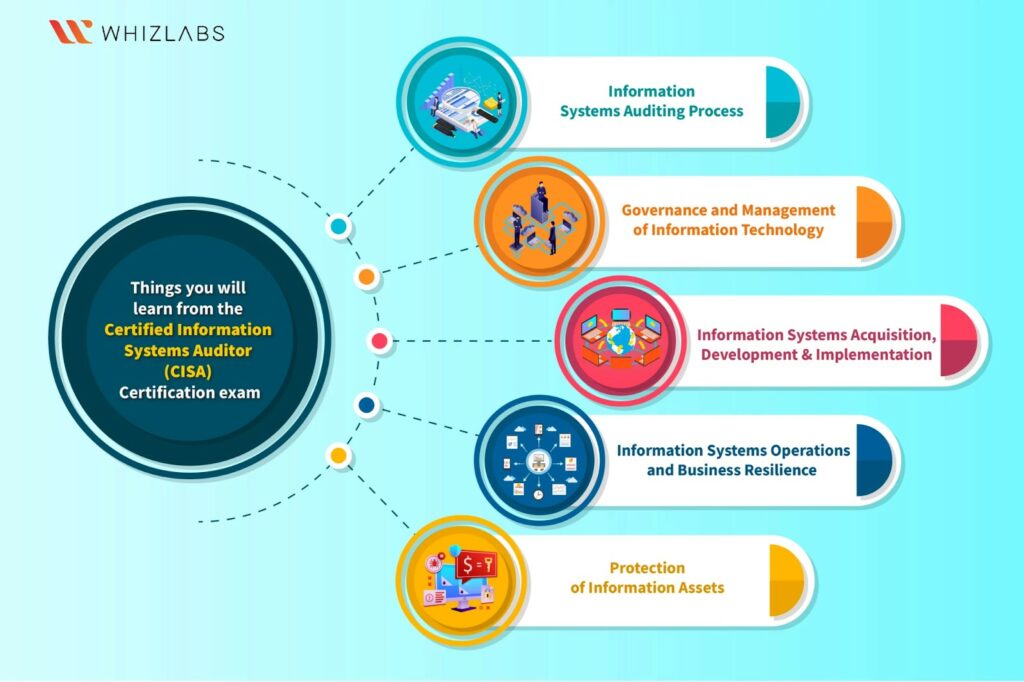
Image source: www.whizlabs.com
1. Information Systems Auditing Process
This domain covers the fundamentals of the information systems audit process, including planning, execution, reporting, and follow-up. Professionals must understand how to conduct audits effectively, ensuring that organizational information systems are secure, reliable, and in compliance with applicable standards.
2. Governance and Management of IT
Governance and management play a crucial role in information security. This domain focuses on the principles of IT governance, the IT management framework, organizational structure, and the alignment of IT strategy with business objectives. Professionals learn how to ensure that IT resources are used responsibly and in line with organizational goals.
3. Information Systems Acquisition, Development, and Implementation
This domain covers the processes involved in acquiring, developing, and implementing information systems. Professionals must understand how to evaluate and test systems during development, ensuring that they meet security and compliance requirements before deployment.
4. Information Systems Operations, Maintenance, and Service Management
Operations, maintenance, and service management are vital aspects of maintaining a secure information environment. This domain addresses the ongoing processes related to system operations, data backup and recovery, incident response, and the management of IT services.
5. Protection of Information Assets
Protecting information assets is a core responsibility in information security. This domain covers the identification and classification of information assets, as well as the implementation of controls to safeguard them. Professionals learn about physical and logical access controls, encryption, and data privacy measures.
How does CISA Certification Benefit in your Career Growth?
1. Comprehensive Knowledge Base

CISA certification is a testament to a professional’s in-depth understanding of information systems and their role in organizational success. Certified individuals possess comprehensive knowledge of audit processes, governance, risk management, and information security controls. This knowledge is crucial for identifying vulnerabilities, ensuring compliance, and implementing effective security measures.
2. Global Recognition

The CISA certification is globally recognized, making it a valuable asset for professionals seeking career opportunities beyond their local borders. Employers worldwide acknowledge the credibility and rigor associated with CISA, giving certified individuals a competitive advantage in the international job market.
3. Alignment with Industry Standards

The CISA certification ensures that professionals are well-versed in industry best practices, standards, and guidelines. This alignment enables certified individuals to contribute effectively to their organizations’ compliance efforts, ensuring that security measures are in line with globally accepted standards.
4. Risk Management Proficiency

Information security professionals with CISA certification are equipped with advanced skills in risk management. This proficiency is crucial in today’s dynamic threat landscape, where organizations face a myriad of cyber risks. Certified individuals can effectively assess and manage risks, safeguarding their organizations against potential threats.
5. Demonstrated Professionalism

Attaining CISA certification requires meeting stringent eligibility requirements, passing a comprehensive exam, and committing to ongoing professional development. This dedication to excellence reflects a high level of professionalism, establishing certified individuals as trusted experts in the field of information security.
How does CISA help in your Career?
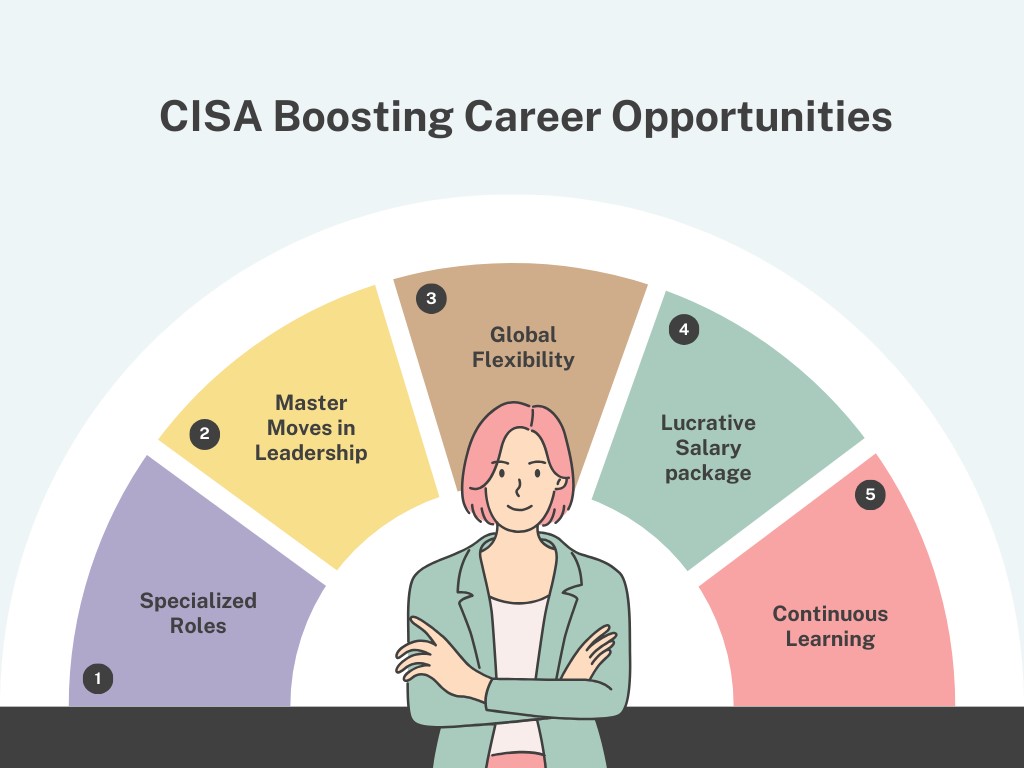
1. Specialized Roles
Get ready to don the detective hat for roles like Information Systems Auditor, IT Auditor, or even the elusive Compliance Analyst. These roles are like solving cyber mysteries, where you assess risks, unveil vulnerabilities, and ensure your organization stays one step ahead of the bad guys.
2. Master Moves in Leadership
Think CISO – Chief Information Security Officer. With CISA, you’re not just solving crimes; you’re leading the charge against cyber villains! Your strategic insights and risk management prowess make you the superhero organizations need to keep their data safe and sound.
3. Global Flexibility
Pack your cyber suitcase because CISA is globally recognized! Your detective skills are in demand worldwide, giving you the freedom to explore opportunities internationally. Who knows? You might be the next cyber detective sensation in Silicon Valley or even the Swiss Alps!
4. Cracking the Salary Safe
Hold on to your cyber hats because CISA-certified folks often enjoy fatter paychecks. Your ability to thwart cyber threats and maintain compliance makes you the true money heist mastermind – except it’s all legal and above board!
5. Continuous Learning
CISA isn’t a one-hit wonder; it’s a lifelong cyber-learning extravaganza! Stay up-to-date on the latest cyber capers and emerging tech trends. Your commitment to continuous learning showcases that you’re not just a one-time hero; you’re in it for the long cyber-haul.
Conclusion
So, fellow cyber sleuths, if you’ve been itching to put on that digital deerstalker cap and shout, “The game is afoot!” – look no further than CISA certification. It’s not just about taking an exam; it’s about transforming yourself into the Sherlock Holmes of information security. Unleash your inner cyber detective, solve digital mysteries, and become the hero organizations need in this ever-evolving cyber landscape. The game is on!
