Table of Contents
ToggleThe designation of Certified Information Systems Auditor (CISA) is internationally acknowledged as a certification for professionals specializing in IS audit control, assurance, and security. Information Systems Audit and Controls Association (ISACA) accredits this CISA certification and is extremely beneficial for professionals in vulnerability assessment and instituting IT controls in an overall enterprise scenario. If you’re also looking to grow in your career, CISA Certification is here to help you.
CISA Training Program and Exam
CISA certification is meant for professionals with five or more years of experience in IS/IT audit, control, assurance, or security; only then can you appear for the CISA Certification. Though experience waivers are available for a maximum tenure of 3 years, then again, it is highly recommended that you opt for CISA training if you have a handsome amount of working experience.
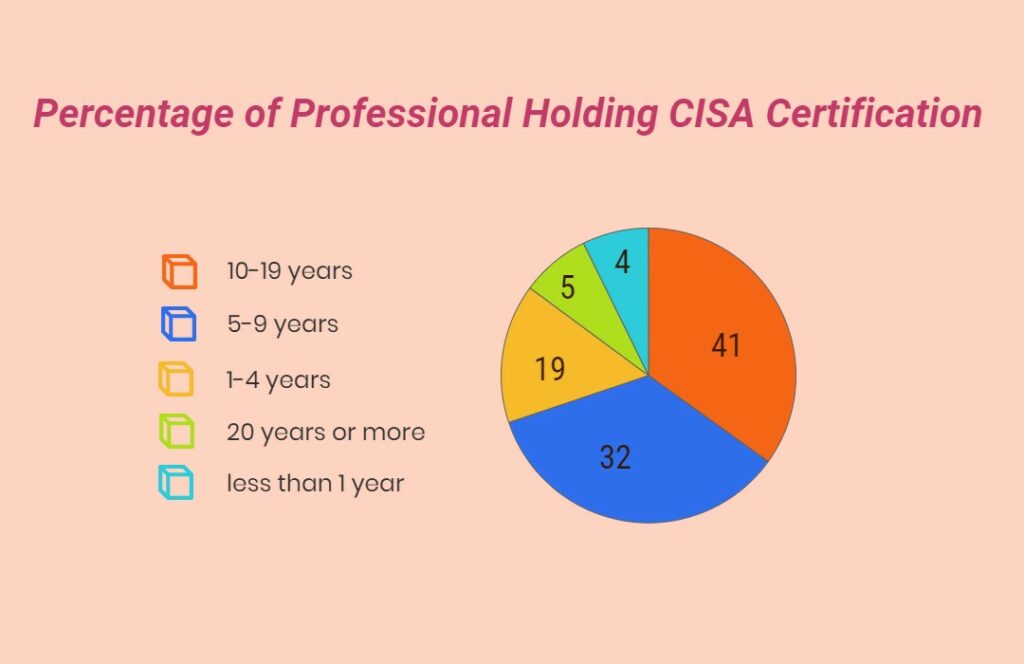
Image source: www.msptraining.com
CISA Syllabus
Domain 1: Information systems audit process- 18%
Domain 2: Governance and management IT- 18%
Domain 3: Information system acquisitions, development, and implementation- 12%
Domain 4: Information system operations and business resilience- 26%
Domain 5: Protection of information assets- 26%
CISA Exam Format
Type of questions: Multiple choice
No. of questions: 240
Exam duration: 4 hours
Passing score: 450 or higher
Languages: Chinese Traditional, Chinese Simplified, English, French, German, Hebrew, Italian, Japanese, Korean, Portuguese, Spanish, Turkish.
Click here to get thorough details of CISA certification accredited by ISACA
How to Pass a CISA Exam?
There are two ways by which you can prepare for the CISA exam. The first thing is self-paced learning where you can refer to ISACA’s CISA preparation guide. The other method is taking coaching under the guidance of CISA-certified trainers who follow the guidelines of ISACA’s CISA syllabus and guidelines. SPOCLEARN offers a 4-day CISA training program to mid-career professionals that can highlight your expertise and affirm your capability to implement a risk-based approach in the planning, execution, and reporting of audit engagements.
Adhere to the following guidelines to pass the CISA Exam easily. To attain the CISA certification, dedicating 4-5 months to self-preparation can prove sufficient.
Here are some strategies to enhance your self-study
- Utilize customizable, interactive sample exams derived from a pool of over 1,000 CISA Review questions to gauge your understanding and readiness.
- For deeper insights, consult the resources offered by CISA, such as the CISA Review Manual by ISACA and the CISA Planning Guide.
- Maximize your self-study effectiveness by taking advantage of the Free CISA self-assessment exam. This will help identify strengths and weaknesses, enabling targeted preparation efforts.
Roles & Responsibilities of a Certified Information Systems Auditor
The core responsibilities of a Certified Information Systems Auditor (CISA) are:
- Formulating an audit strategy for information systems (IS) grounded in risk management principles.
- Strategizing audits to assess the protection, management, and value of IT assets.
- Executing audits in alignment with the organization’s established standards and objectives.
- Communicating audit findings and delivering recommendations to management based on assessment outcomes.
- Conducting follow-up audits to verify the implementation of recommended actions by management.
Moreover, CISAs are tasked with broader duties beyond audit control. They collaborate with management to validate organizational processes, implementation plans, and system operations while advancing organizational objectives and strategies.
This involves assessing
- Practices in risk management.
- IT portfolio and resource management.
- Strategies for aligning business and IT objectives.
- Business continuity and disaster recovery plans.
- IT policies, standards, processes, and procedures.
- The effectiveness of the IT control framework.
- Management and oversight of IT personnel, organizational structure, and controls.
Post-implementation, CISAs continue to oversee various aspects to ensure the successful deployment of systems. This includes conducting project and post-implementation reviews and evaluating:
- The business case for the system.
- IS controls.
- IT supplier selection and contract management.
- The project management framework and controls.
- IS preparedness.
Upon system implementation, CISAs assess
- IT service management practices and structure.
- End-user computing.
- Change and release management operations.
- IT continuity and resilience.
- Execution of database management systems.
- IT operations and maintenance.
- Reviews of the IS.
- Incident management practices and complications.
- Data quality and lifecycle management.
Ultimately, CISAs collaborate with management to uphold security standards, policies, procedures, and controls within the organization, ensuring the integrity, confidentiality, and availability of information assets.
Maintaining the CISA Certification
CISA candidates and certified professionals are obligated to adhere to ISACA’s Continuing Professional Education (CPE) program, which aims to ensure their ongoing relevance and proficiency in the field.
The objectives of the CPE program are:
- Monitoring the maintenance of knowledge and competencies among IS audit, control, and security professionals.
- Distinguishing qualified CISAs from individuals who haven’t fulfilled the requirements and are ineligible to maintain their certification.
- Assisting senior management in establishing robust IS audit, control, and security functions by offering recommendations and criteria for personnel selection, training, and development.
- Sustaining the expertise of individual CISAs by continually updating their knowledge and skills in IS auditing, control, and security.
ISACA mandates the payment of maintenance fees and a minimum of 20 CPE hours annually, along with an additional 120 contact hours over a fixed three-year period.
Benefits of CISA Certification
Here are more detailed benefits explained:
1. Better Potential
In the field of Information Security, IT auditing requires people who are comfortable with various technologies. Since information systems are crucial in today’s evolving business landscape, having the CISA certification shows employers and clients that you can adapt and thrive in this dynamic environment.
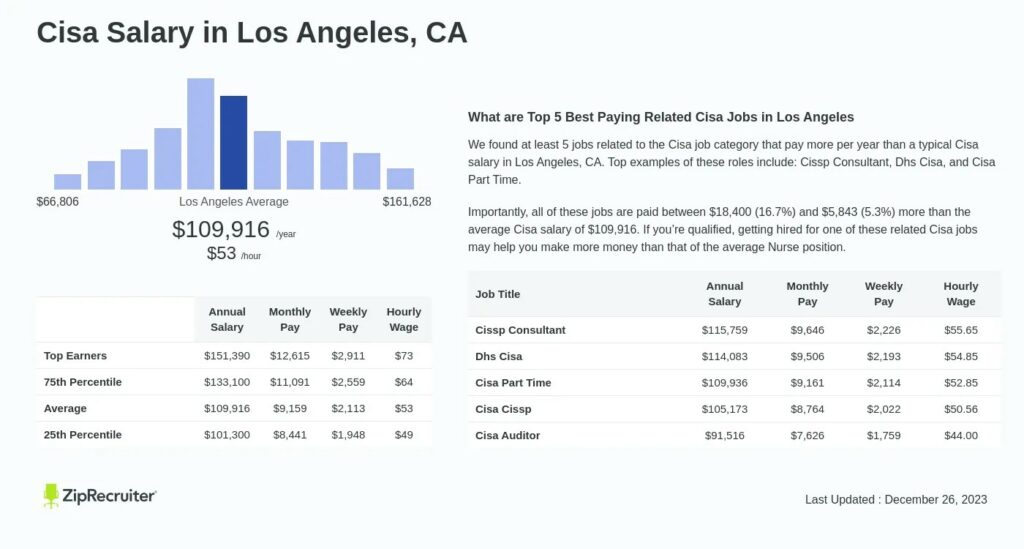
2. Higher Salary
Certified IT auditors with CISA certification often earn higher salaries compared to other auditors. Indeed UK reports that CISA IT Auditors with intermediate to high-level experience can earn between £70,000 to £140,000 annually, and Morgan McKinley states the average salary range for IT Auditors is between £55,000 to £70,000 annually.
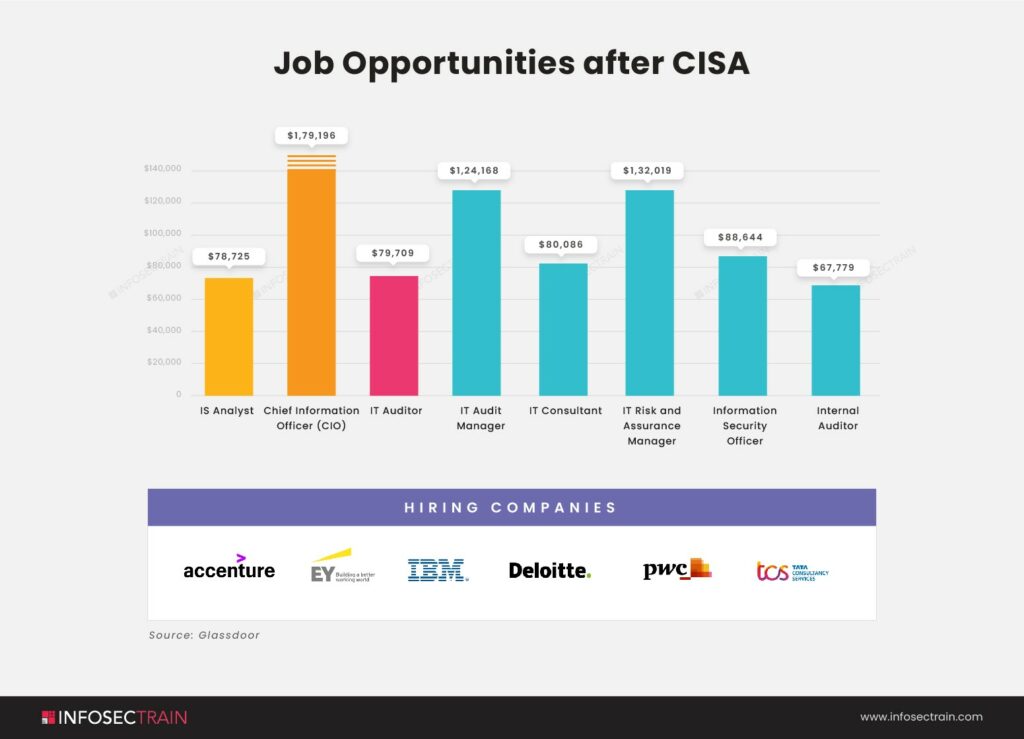
Image source: www.infosectrain.com
3. Multiple Job Opportunities
The Information Security industry is always growing, creating new opportunities for IT auditors. By obtaining the CISA certification, professionals can advance in their careers, aiming for top managerial positions like Chief Information Officer (CIO).
4. Internationally Recognized Certification
CISA certification is highly regarded globally, giving certified professionals a competitive edge in the auditing field. This recognition allows professionals to pursue employment opportunities worldwide, adapting to the globalized economy’s demands.
5. Specialized Expertise
As the IT industry expands rapidly, there is a growing need for certified professionals like CISA-certified IT auditors who can analyze and protect information system assets. Some employers even require CISA certification for certain roles, seeing it as a mark of dedication and seriousness in the field.
6. Enhanced Skill Set
CISA-certified professionals gain expertise in implementing and evaluating governance standards in IT, understanding organizational structures, measures, and control practices for IT governance. They also learn best practices in management for testing, implementing, and maintaining infrastructures aligned with organizational objectives.
Conclusion
In conclusion, obtaining the Certified Information Systems Auditor (CISA) certification offers numerous benefits in today’s dynamic Information Security industry. From standing out in a rapidly evolving field to commanding higher salaries and accessing a wide range of job opportunities, CISA-certified professionals are well-equipped to excel in their careers. The global recognition of the certification further enhances their competitiveness in the job market, while specialized expertise and additional skills acquired through CISA training ensure their relevance and value in addressing the evolving needs of organizations. Overall, the CISA certification serves as a testament to an individual’s dedication, expertise, and adaptability in the realm of IT auditing and information systems management.
